Konferencje i wydarzenia specjalne
Szkolenia podczas #ilovemkt
Szkolenia z Pawłem Tkaczykiem
Najpopularniejsze szkolenia
Nowości
Szkolenia z marketingu i reklamy w internecie
Szkolenia HR
Szkolenia organizowane tylko w formie dedykowanej
Nagrania video

59 wystąpień
2670 zł
Materiały video z XVI edycji konferencji

20 wystąpień
1470 zł
Pakiet TOP20 prelekcji z XVI edycji konferencji

48 wystąpień
2170 zł
Materiały video z XV edycji konferencji

20 wystąpień
1470 zł
Pakiet TOP20 prelekcji z XV edycji konferencji
Czy wiesz, że możesz otrzymać nawet do 8500 zł dofinansowania?
Chętnie odpowiem na Twoje pytania i pomogę w formalnościach.
Monika.Bartnikowska@sprawnymarketing.pl +48 577 331 077
Monika
Bartnikowska
Customer Care Specialist

Kalendarium szkoleń
Rejestrując się 5 dni przed szkoleniem swój certyfikat otrzymasz po szkoleniu w formie elektronicznej.
(aby otrzymać certyfikat w wersji drukowanej, należy zapisać się z minimum tygodniowym wyprzedzeniem – dotyczy tylko szkoleń stacjonarnych)
Wybierając pakiet szkoleniowy, zwróć uwagę na dostępne bonusy. Sprawdź jakie korzyści wynikają z zestawu VIP, a jakie ze standardowego - dokonaj najkorzystniejszego dla siebie wyboru.
Wybierz szkolenie i zobacz, jakie bonusy czekają na Ciebie:
Bonusy w ramach pakietów
VIP
Standard

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet prelekcji Pawła Tkaczyka podczas wszystkich edycji konferencji I ❤️ Marketing, które uzupełniają tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Podstawy analityki internetowej, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Podstawy analityki internetowej, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Marketing w wyszukiwarkach, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Marketing w wyszukiwarkach, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Sklep internetowy, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Sklep internetowy, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Sklep internetowy, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Marketing w wyszukiwarkach, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Marketing w wyszukiwarkach, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Marketing w wyszukiwarkach, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet prelekcji Pawła Tkaczyka podczas wszystkich edycji konferencji I ❤️ Marketing, które uzupełniają tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet prelekcji Pawła Tkaczyka podczas wszystkich edycji konferencji I ❤️ Marketing, które uzupełniają tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet materiałów video Social Media Marketing, uzupełniający tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet prelekcji Pawła Tkaczyka podczas wszystkich edycji konferencji I ❤️ Marketing, które uzupełniają tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet prelekcji Pawła Tkaczyka podczas wszystkich edycji konferencji I ❤️ Marketing, które uzupełniają tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing

Pakiet prelekcji Pawła Tkaczyka podczas wszystkich edycji konferencji I ❤️ Marketing, które uzupełniają tematykę szkolenia

Roczna elektroniczna prenumerata magazynu sprawny.marketing

Dostęp do Premium sprawny.marketing na 6 miesięcy

Certyfikat potwierdzający udział w szkoleniu

Prezentacja trenera w formacie PDF

Egzemplarz magazynu sprawny.marketing

Dostęp do MKTletter’a (jeśli zapiszesz się do newslettera podczas rejestracji)
Dedykowane rabaty narzędziowe
Zestaw materiałów biurowych sprawny.marketing
Zobacz kalendarium eventów
Pobierz kalendarium eventów sprawny.marketing na 2023 rok i bądź na bieżąco z wydarzeniami marketingowymi!
Pobierz kalendarium eventówWiedza z naszych szkoleń jest wykorzystywana m.in w następujących firmach:
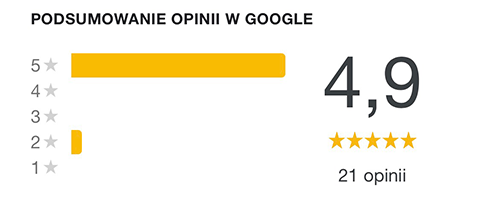
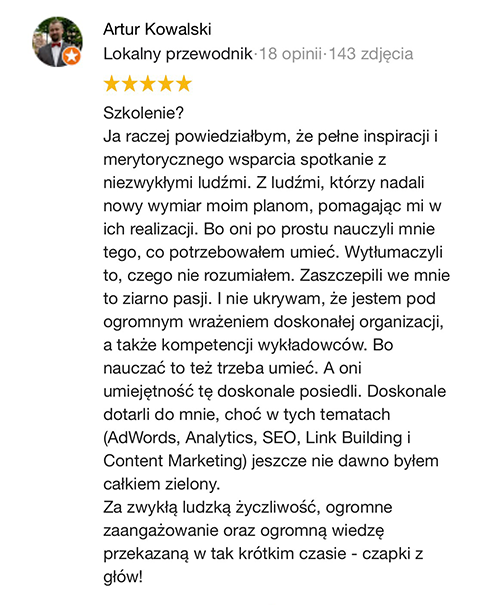
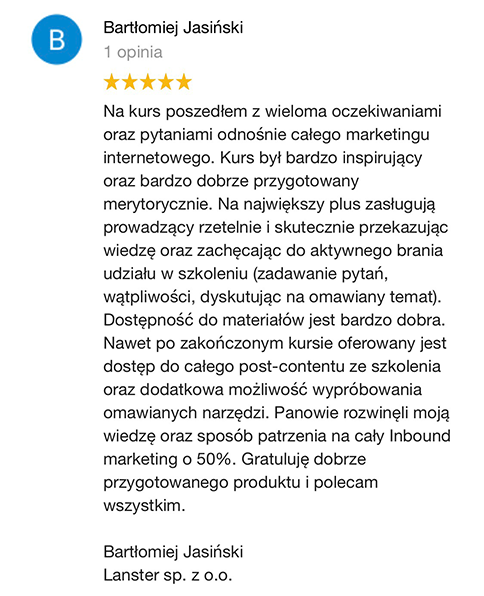
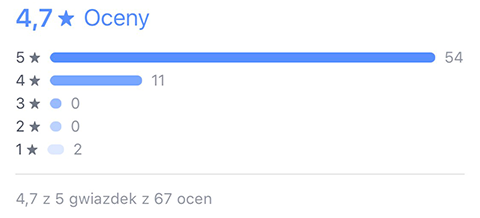
Opinie uczestników naszych szkoleń


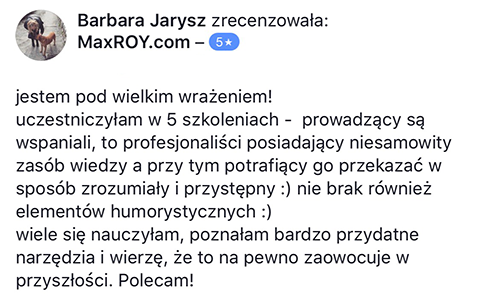
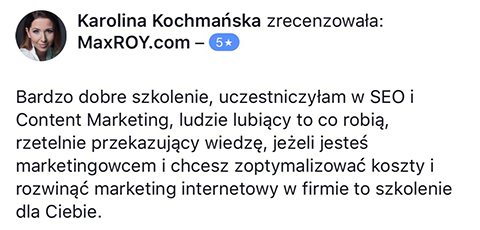
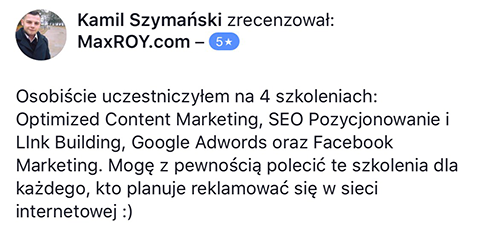
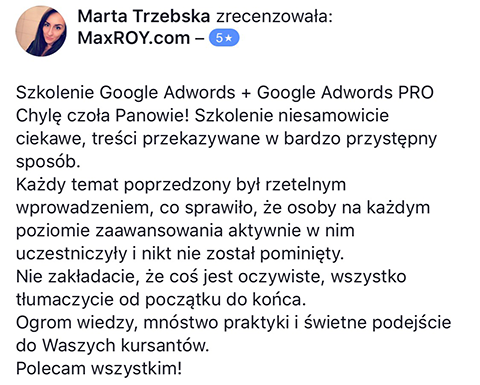

Szkolenie Marcina oparte jest na jego kilkuletnich doświadczeniach. Nie teoretyzuje. Podaje na tacy gotowe rozwiązania. Dzięki temu mogłem skonfrontować moje teoretyczne wyobrażenia z praktyką. I po raz kolejny utwierdziłem się w przekonaniu, że poleganie na własnej intuicji, zaleceniach ergonomicznych itp. jest bardzo zwodnicze i ma niewiele wspólnego z zarabianiem na AdSense. Mam wrażenie, że Marcin oszczędził mi dużo czasu, który musiałbym poświęcić na własne testy. - "Jak zarabiać na stronach internetowych?"
Szkolenie z social media opierało się przede wszystkich na praktycznych przykładach dostarczając mi solidnej dawki wiedzy dotyczącej tego, jakich użytkowników mogę spotkać na poszczególnych platformach, jak można ich scharakteryzować i jak będą wyglądać trendy w social media. Case studies dało mi inspirację, którą być może wykorzystam w działaniach firmy, dla której pracuję. - Marketing w Social Media
Lokalizacja szkoleń
Poznań Novotel, plac Andersa 1, 61-898
Warszawa ADN Centrum Konferencyjne ul. Grzybowska 56, 00-844 Warszawa
Wrocław Ibis Styles ,plac Konstytucji 3 Maja 3, 50-083 Wrocław
Kraków Q Hotel Plus Kraków, ul. Wygrana 6, 30-311 Kraków
Gdańsk Hotel Sadova, Łąkowa 60, 80-769 Gdańsk.

































































































